-
Security Vulnerability Patch카테고리 없음 2020. 3. 3. 21:22
Worms are the cause of many cyber headaches. They can easily replicate themselves to spread malicious malware to other computers in your network.
As the field responders providing Microsoft enterprise customers with onsite assistance to serious cybersecurity threats, our Detection and Response Team (DART) has seen quite a few worms. If you’ve, then you know your worms are our concern and that’s why we keep an eye out for BlueKeep. Protect against BlueKeepThis summer, the DART team has been preparing for, colloquially known as BlueKeep, and has some advice on how you can protect your network. The BlueKeep vulnerability is “wormable,” meaning it creates the risk of a large-scale outbreak due to its ability to replicate and propagate, similar to. Conficker has been widely estimated to have impacted 10- to 12-million computer systems worldwide. WannaCry was responsible for approximately $300 million in damages at just one global enterprise.To protect against BlueKeep, we strongly recommend you apply the, which includes a patch for the vulnerability.
If you use Remote Desktop in your environment, it’s very important to apply all the updates. If you have Remote Desktop Protocol (RDP) listening on the internet, we also strongly encourage you to move the RDP listener behind some type of second factor authentication, such as VPN, SSL Tunnel, or RDP gateway.You also want to enable Network Level Authentication (NLA), which is a mitigation to prevent un-authenticated access to the RDP tunnel. NLA forces users to authenticate before connecting to remote systems, which dramatically decreases the chance of success for RDP-based worms. The DART team highly recommends you enable NLA regardless of this patch, as it mitigates a whole slew of other attacks against RDP.If you’re already aware of the BlueKeep remediation methods, but are thinking about testing it before going live, we recommend that you. It’s important to note that the exploit code is now publicly and widely available to everyone, including malicious actors.
Security Vulnerability Patch 1
By exploiting a vulnerable RDP system, attackers will also have access to all user credentials used on the RDP system. Why the urgency?Via open source telemetry, we see more than 400,000 endpoints lacking any form of network level authentication, which puts each of these systems potentially at risk from a worm-based weaponization of the BlueKeep vulnerability.The timeline between patch release and the appearance of a worm outbreak is difficult to predict and varies from case to case. As always, the DART team is ready for the worst-case scenario. We also want to help our customers be prepared, so we’re sharing a few previous worms and the timeline from patch to attack. Hopefully, this will encourage everyone to patch immediately.Learn moreTo learn more about DART, our engagements, and how they are delivered by experienced cybersecurity professionals who devote 100 percent of their time to providing cybersecurity solutions to customers worldwide, please contact your account executive.

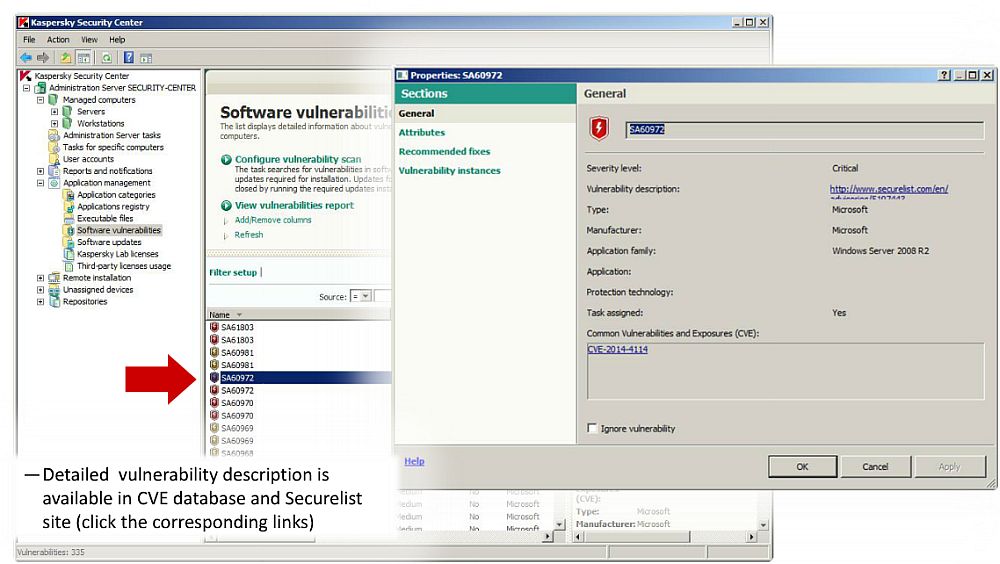
Security Vulnerability Report
What Is Patch File
Bookmark the to keep up with our expert coverage on security matters. Also, follow us at for the latest news and updates on cybersecurity.This document is for informational purposes only and Microsoft makes no warranties, express or implied, in this blog.Filed under:.,.,.,.,.